A virtual private network is a great way to keep your internet usage secure and private whether at home or on public Wi-Fi. But just how private is your activity over a VPN? How do you know if the VPN is doing its job or if you’re unwittingly leaking information to those trying to pry into your activities?
One simple way to see if the VPN is working is to search for what is my IP on Google. At the top of the search results, Google will report back your current public Internet Protocol (IP) address. If you’re on a VPN, it should show the VPN’s IP. If it doesn’t, you know you have a problem.
Note: If you’re not sure what your VPN’s actual IP is then take the IP address Google gives you (such as 107.152.98.165) and enter that into Google like so: IP 107.152.98.165. The top several search results should indicate where that IP is located. If you’re in Toronto and the IP is registered in California then the VPN is working.
Diving deeper
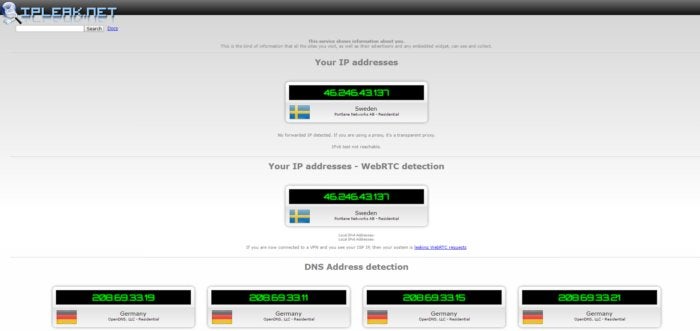
Your public IP address is just one way private information can leak over a VPN. To see how fully private you are visit IPLeak.net. This website checks a number of ways that your IP address and other information can leak, including over WebRTC (an up-and-coming browser-based chat technology), DNS leaks, torrenting, and geolocation.
Not all of these tests happen automatically. The torrent test, for example, requires a small torrent file (available via magnet link) to see if torrents are funneling through your VPN or not.
The geolocation test is helpful, but keeping your location secure is pretty straightforward. Just don’t allow any website to use your location while on a VPN. One way to do that is to specify a browser, Firefox for example, as your VPN-only browser. Then disallow location requests on that browser. Alternatively, you could use a browser extension that provides a fake location to websites that request it.
The most likely culprit in leaked information, however, is via the Domain Name System (DNS). To navigate the web, your machine requires contact with DNS servers to help translate website addresses from names to numeric IP addresses. Typically a PC automatically uses the DNS servers of your internet service provider. The problem is that if you’re using a VPN and leaking DNS through a local service provider, you can reveal enough information to point anyone spying on you in the right direction.
Many set-it-and-forget-it type VPNs funnel your DNS requests through their own servers, though some require an explicit settings change to do this. Check your VPN provider’s help pages if you are leaking DNS for advice on how to fix it.
Another way to address this issue is to permanently switch to an alternative DNS provider such as Google, OpenDNS, or Comodo Secure DNS.
Once you’ve fixed your DNS problems, return to IPLeak to see what it reports. If it shows DNS servers that aren’t related to your ISP or general location then you’re all set to enjoy added privacy over your VPN connection.
